In today’s digital age, cloud technology has become an integral part of many organizations. With the growing use of cloud applications and services, it is crucial to ensure secure access control to protect sensitive data and prevent unauthorized access.
Cloud identity management is a critical aspect of securing access control in the cloud. In this article, we will discuss the top best practices for cloud identity management, including authentication, authorization, and access control policies, to ensure that your organization’s data remains secure in the cloud.
Cloud identity management is vital to secure access control in the cloud environment. The top best practices for cloud identity management include implementing multifactor authentication, regularly reviewing access controls, managing privileged access, and enforcing strong password policies. Additionally, regularly monitoring and analyzing access logs can help identify and prevent potential security threats.

The Top Cloud Identity Management Best Practices for Secure Access Control
Cloud identity management is quickly becoming a critical component in securing access control for organizations worldwide. With the increasing adoption of cloud computing, managing and securing identities has become a major challenge for most enterprises. In this article, we will explore the top cloud identity management best practices that organizations can implement to ensure secure access control.
1. Implement Strong Password Policies
A strong password policy is the foundation of secure access control. Organizations should enforce password policies that require users to create complex passwords that include a combination of uppercase and lowercase letters, numbers, and special characters. Passwords should be changed frequently, and users should not reuse the same password across multiple accounts. Implementing two-factor authentication can also provide an extra layer of security.
Organizations can use password management tools to help enforce strong password policies. These tools can generate and store complex passwords, as well as authenticate users with biometric data.
2. Use Role-Based Access Control
Role-based access control (RBAC) is a popular method of controlling access to resources based on the roles and responsibilities of users within an organization. RBAC allows organizations to assign permissions based on job functions, which helps to ensure that users only have access to the resources they need to perform their job duties.
Implementing RBAC can be challenging for organizations with complex structures, but it can significantly reduce the risk of unauthorized access.
3. Implement Multi-Factor Authentication
Multi-factor authentication (MFA) is an essential component of secure access control. MFA requires users to provide more than one form of authentication before accessing resources. This can include something the user knows, such as a password or PIN, something the user has, such as a badge or token, or something the user is, such as biometric data.
Implementing MFA can significantly reduce the risk of unauthorized access, especially in cases where passwords may have been compromised.
4. Regularly Review and Update Access Controls
Access controls should be reviewed and updated regularly to ensure that they remain effective. This includes reviewing user access privileges, removing access for users who no longer require it, and updating access controls to reflect changes in job responsibilities.
Organizations should also regularly review and update their policies and procedures to ensure that they reflect the latest best practices and comply with regulatory requirements.
5. Use Single Sign-On
Single sign-on (SSO) allows users to authenticate once and access multiple applications and services without having to authenticate again. SSO can streamline the authentication process and reduce the risk of password fatigue and user error.
Implementing SSO can be challenging for organizations with multiple applications and services, but it can significantly improve the user experience and reduce the risk of unauthorized access.
6. Implement Identity Governance and Administration
Identity governance and administration (IGA) is a process that enables organizations to manage and control user access to resources. IGA includes the identification, authentication, authorization, and certification of user access.
Implementing IGA can help organizations to streamline their access control processes, reduce the risk of unauthorized access, and comply with regulatory requirements.
7. Use Cloud Access Security Brokers
Cloud access security brokers (CASBs) provide organizations with visibility and control over their cloud applications and services. CASBs can help to identify and block unauthorized access attempts, enforce security policies, and monitor user activity.
Implementing CASBs can help organizations to secure their cloud environments and reduce the risk of unauthorized access.
8. Conduct Regular Security Audits
Regular security audits can help organizations to identify vulnerabilities and weaknesses in their access control processes. Audits should include a review of user access privileges, password policies, RBAC implementation, and other security controls.
Organizations should also conduct penetration testing to identify potential security gaps and test the effectiveness of their access control processes.
9. Provide User Awareness Training
User awareness training is an essential component of a secure access control program. Users should be educated on the importance of strong passwords, the risks of sharing passwords, and the importance of reporting suspicious activity.
Organizations should also provide training on the use of multi-factor authentication and the importance of keeping their access credentials secure.
10. Leverage Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) can be used to identify and block suspicious activity, automate access controls, and improve the overall security of an organization’s access control processes.
AI and ML can help organizations to detect and respond to threats in real-time, reducing the risk of unauthorized access and data breaches.
In conclusion, implementing these cloud identity management best practices can significantly improve an organization’s access control processes and reduce the risk of unauthorized access. Organizations should regularly review and update their access control processes to ensure that they remain effective and comply with regulatory requirements.
Frequently Asked Questions
Here are some frequently asked questions about the top cloud identity management best practices for secure access control:
What is cloud identity management?
Cloud identity management refers to the processes and tools used to manage user identities and access control in cloud-based environments. It involves authenticating users, granting or revoking access privileges, and monitoring user activity to ensure security and compliance. Cloud identity management solutions are designed to provide centralized control over user access to cloud resources, regardless of their location or device.
Best practices for cloud identity management include implementing strong authentication mechanisms, enforcing access policies based on user roles and responsibilities, and regularly reviewing and updating access privileges to ensure they align with business needs and security policies.
What are the benefits of using cloud identity management?
Cloud identity management offers several benefits for organizations, including improved security, increased flexibility and scalability, and reduced IT overhead. By centralizing user identity and access management in the cloud, organizations can simplify the management of access privileges, reduce the risk of unauthorized access, and improve compliance with data protection regulations.
Cloud identity management also enables organizations to scale their IT infrastructure more easily, allowing them to add or remove users and resources as needed without incurring significant costs or disruptions. Additionally, it can help reduce the burden on IT staff by automating routine tasks, such as user provisioning and access requests.
What are the top best practices for secure access control in cloud identity management?
Some of the top best practices for secure access control in cloud identity management include implementing strong authentication mechanisms, such as multi-factor authentication, to verify user identity; enforcing access policies based on user roles and responsibilities; and regularly reviewing and updating access privileges to ensure they align with business needs and security policies.
Other best practices include implementing granular access controls, such as attribute-based access control, to provide more fine-grained control over user access to cloud resources; monitoring user activity to detect and respond to suspicious behavior; and integrating cloud identity management with other security solutions, such as security information and event management (SIEM) systems.
What are the risks of not implementing cloud identity management best practices?
Not implementing cloud identity management best practices can expose organizations to a range of security risks, including unauthorized access to sensitive data or systems, data breaches, and compliance violations. Without proper user authentication and access controls, attackers can exploit weak passwords or stolen credentials to gain access to cloud resources and steal or manipulate data.
Additionally, without proper monitoring and review of access privileges, organizations can inadvertently grant unnecessary or excessive access to users, increasing the risk of data leakage or insider threats. Failure to comply with data protection regulations, such as GDPR or CCPA, can also result in significant fines and reputational damage.
How can organizations ensure compliance with data protection regulations when using cloud identity management?
To ensure compliance with data protection regulations when using cloud identity management, organizations should implement strong access controls and user authentication mechanisms, such as multi-factor authentication, to verify user identity and limit access to sensitive data. They should also regularly review and update access privileges to ensure they align with business needs and security policies.
Organizations should also maintain detailed logs of user activity and access requests, and implement monitoring and alerting mechanisms to detect and respond to suspicious behavior. Finally, they should ensure that their cloud identity management solution is compliant with relevant data protection regulations, such as GDPR or CCPA, and that they have appropriate policies and procedures in place to respond to data breaches or other security incidents.
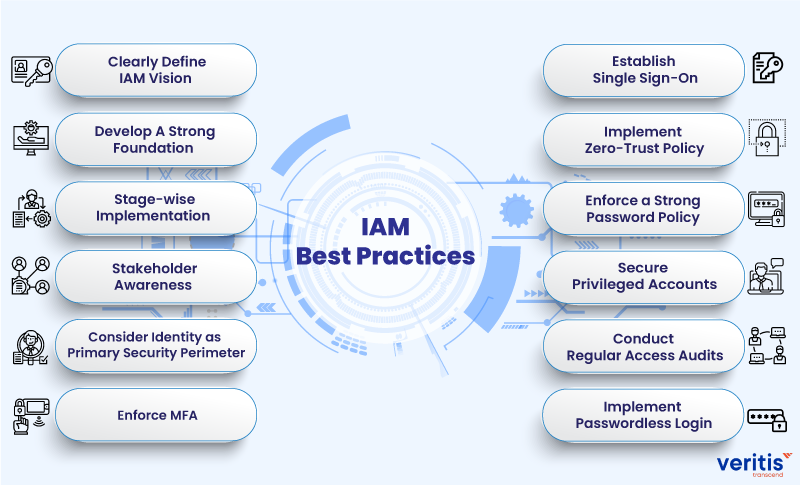
In conclusion, implementing cloud identity management best practices is crucial for ensuring secure access control in today’s digital age. By following the top practices outlined above, organizations can reduce the risk of data breaches, protect sensitive information, and maintain regulatory compliance.
Firstly, it’s important to prioritize multi-factor authentication to ensure that only authorized users can access sensitive information. Secondly, utilizing role-based access control can help organizations limit access to sensitive data based on an individual’s job responsibilities. Finally, regular monitoring and auditing of access logs can help detect and respond to any unauthorized access attempts.
In conclusion, organizations should not underestimate the importance of cloud identity management best practices when it comes to securing access control. By adopting these practices, organizations can stay ahead of potential security threats and safeguard their sensitive information from unauthorized access.
